Job seekers and digital marketers are increasingly exploited by threat actors posing as recruiters. In one of the latest campaigns, BatShadow has turned to a Go-based malware strain Vampire Bot to ensnare targets through deceptive job offers and multi-layered infection chains.
The sophistication of this operation lies in its disguise: innocent-looking documents, ZIP archives, and coerced browser redirects. As a veteran cybersecurity observer, I break down how this campaign unfolds, the techniques behind it, and how defenders can detect and block it effectively.
BatShadow’s Evolving Tactics
BatShadow has previously deployed malware such as Agent Tesla, Lumma Stealer, and Venom RAT under domains like samsung-work[.]com.
Trend watchers have tied its activity to Vietnamese threat groups focused on monetization and account hijacking. Digital marketing professionals are frequent prey thanks to their access to business assets.
With Vampire Bot, BatShadow levels up its tactics this time wielding a custom Go-based payload wrapped in elaborate social engineering designed for job-seeker engagement.
Fake Recruiter Lures & File Packaging
Attackers begin by sending ZIP archives that impersonate legitimate job descriptions. Inside: a decoy PDF plus a malicious file disguised either as an LNK or .pdf.exe.
Opening the LNK triggers embedded PowerShell. That script retrieves additional components including the actual payload and the lure PDF from attacker infrastructure. The execution masquerades as legitimate activity while secretly enabling a chain of infection.
LNK → PowerShell → Payload Delivery
Once the LNK is invoked, PowerShell fetches:
-
A lure PDF (e.g. marketing job content)
-
A ZIP containing tools (e.g. XtraViewer) for remote access
The ZIP payload typically includes a deceptive .pdf.exe file padded to resemble a legitimate PDF. The Go-based Vampire Bot executable then runs, initiating host profiling, screenshot capture, command control, and possible lateral expansion.
The actor uses a C2 domain: api3.samsungcareers[.]work for control and instructions.
Vampire Bot can collect system metadata, capture periodic screenshots, and execute remote commands.
Its design emphasizes low visibility and persistence under the radar.
To cloak its identity, the domain used for C2 mimics benign naming (samsungcareers), increasing likelihood of bypassing cursory inspection. It also uses flexible payload channels, meaning the bot can fetch further tools or commands as needed.
Social Engineering & Browser Redirect Strategy
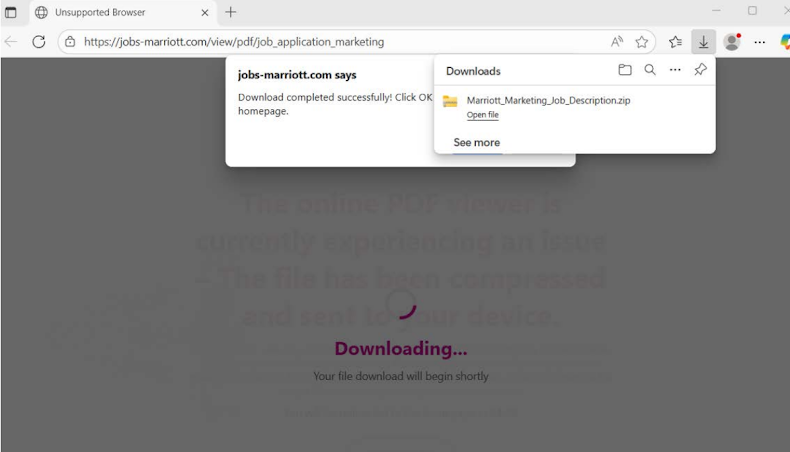
A critical twist: after opening the lure, victims are redirected to a page claiming their browser is unsupported. They are instructed to launch Microsoft Edge and paste the URL manually.
This trick defeats default script blocking in Chrome and enforces user action allowing the attacker’s redirect to proceed as “user-initiated.”
Once Edge is in use, the attacker triggers a fake error claiming the PDF viewer fails, then auto-downloads the malicious ZIP file. Thus, the victim unwittingly launches the payload, believing the process is legitimate.
BatShadow’s link to Vietnam is reinforced via IP address 103.124.95[.]161, previously tied to Vietnamese-affiliated campaigns. Their historical targeting of digital marketers and job-seeking communities further aligns with this new method.
Observables to watch for include:
-
Domains like
samsungcareers[.]work -
LNK files alongside legitimate-seeming PDFs
-
Scripts that force Edge or browser-switch instructions
Defensive Strategies & Mitigation
-
Email filtering & sandboxing: Block or sandbox ZIPs containing LNK or double-extension files.
-
Endpoint detection: Monitor PowerShell invocations from unexpected contexts.
-
Browser behavior analytics: Flag unusual redirects or forced browser changes.
-
User education: Warn job seekers about resume/email attachments and social engineering lures.
By combining these layers, defenders can cut off the attack chain before persistent malware takes hold.
The BatShadow Vampire Bot campaign highlights how threat actors adapt to exploit trust and opportunity. Job seekers represent a unique social engineering vector one few expect to be weaponized.
With Go-based malware, elaborate browser coercion, and meticulous reconnaissance, this campaign demands defenders stay alert and strategize detection from multiple vantage points.
FAQs
Q1. What is Vampire Bot?
Vampire Bot is a Go-based malware strain capable of profiling, screenshot capture, command execution, and data exfiltration.
Q2. How do attackers reach job seekers?
They send fake recruiter emails, disguised ZIP files, and lure victims with promises of job descriptions.
Q3. What is the infection chain (TTP)?
LNK triggers PowerShell → downloads payload ZIP → executes .pdf.exe → installs Vampire Bot.
Q4. How can a job seeker avoid this?
Never open suspicious executables or LNK files; inspect attachments carefully; verify recruiter identities independently.
Q5. Are there known detection signatures yet?
Indicators such as odd domain names, file pads between .pdf and .exe, and forced Edge redirects are early signals threat intel may publish more soon.










