
Confucius APT Unleashes WooperStealer, Anondoor in Pakistan
Confucius hackers launched a phishing campaign in Pakistan deploying WooperStealer and Anondoor malware using PPSX and LNK files to compromise sensitive systems.

Confucius hackers launched a phishing campaign in Pakistan deploying WooperStealer and Anondoor malware using PPSX and LNK files to compromise sensitive systems.

The PyPI “SoopSocks” package claims to be a SOCKS5 proxy solution but conceals backdoor capabilities, enabling attackers to control compromised systems remotely.

A newly discovered Android banking trojan combines overlay attacks with a stealthy hidden VNC server to gain full remote control over compromised devices.
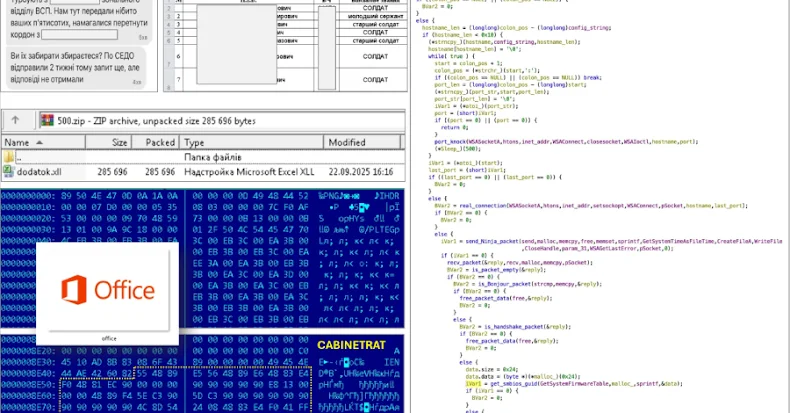
Ukraine’s CERT-UA has warned that CabinetRAT backdoor malware is being actively deployed in cyber espionage campaigns targeting government and critical networks.

Researchers have uncovered a new cybercriminal toolkit called MatrixPDF, designed to transform normal PDF files into weapons for phishing and malware delivery. This toolkit lowers the barrier for attackers. In fact, it provides ready made templates that let even inexperienced hackers craft PDF lures capable of bypassing security filters. As a result, phishing campaigns become…
A malicious MCP server can exfiltrate API keys and sensitive data from applications, exposing how trust in developer frameworks can be abused.

Hackers posing as Medusa agents tried to lure BBC’s Joe Tidy into facilitating a cyberattack, offering him 15–25% of ransom payouts in exchange for his laptop’s access to the network.

Threat actors are increasingly poisoning AI tools and assistants embedding dangerous prompts or corrupting the data they rely on to turn defenses against organizations.

A rapid cascade of cyber events Chrome zero-day, a record DDoS, Cisco IOS exploit, and Kali Linux upgrade highlight how threat activity keeps accelerating.

A sophisticated cyber campaign used DLL side‑loading to deliver a hybrid PlugX variant and the Bookworm backdoor to telecom and ASEAN networks, revealing renewed tactics by China‑linked threat actors.