The newly disclosed WireTap attack shows how a passive DDR4 memory-bus interposer can extract Intel SGX attestation secrets from servers with physical access. By forcing the DIMM to operate at lower frequencies and observing encrypted traffic, researchers from Georgia Tech and Purdue reconstruct the ECDSA nonce used in SGX DCAP attestation, then derive the private attestation key undermining trust in affected deployments.
Unlike classic speculative-execution attacks, WireTap doesn’t rely on microarchitectural bugs. Instead, it uses a physical interposer to passively read ciphertext patterns on the DRAM bus, then leverages the determinism of AES-XTS on DDR4 to build a ciphertext dictionary for targeted operations inside the enclave. read more about WireTap
How the WireTap attack works
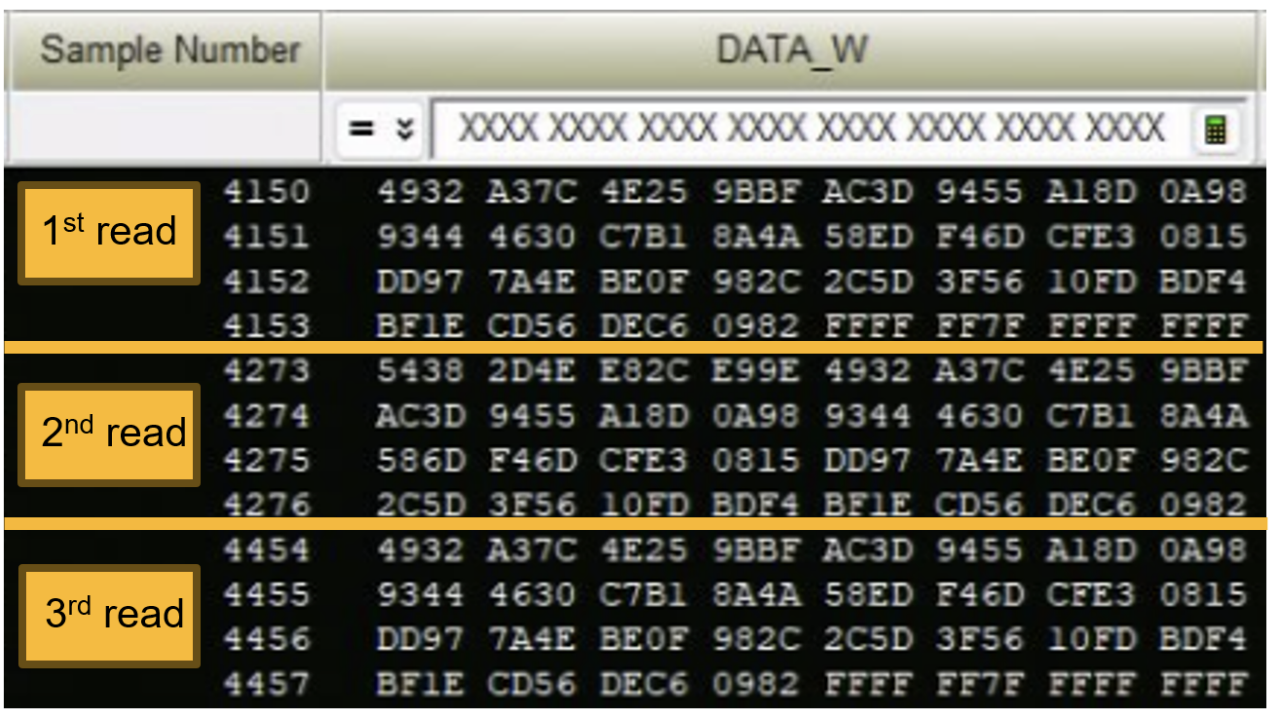
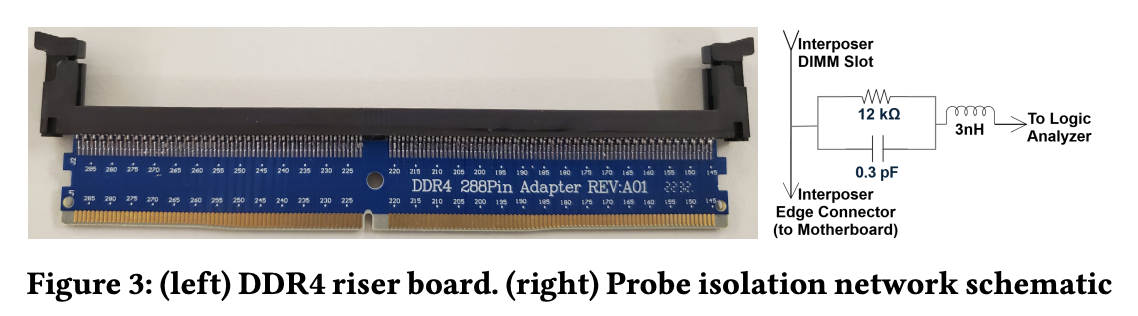
The attack mounts a DIMM-riser interposer between CPU and memory, down-clocks the bus via SPD metadata tweaks, and captures traffic with a low-cost logic analyzer. During enclave signing, the team triggers SGX to generate an ECDSA signature and then identifies the corresponding ciphertext sequences for the nonce k. With k recovered, ECDSA private key extraction follows from standard math.
Intel acknowledges WireTap (and a related Battering RAM study) as physical interposer attacks that fall outside SGX’s threat model. Intel notes no CVE is planned, advises understanding SGX’s physical assumptions, and points to TME-MK integrity modes on newer Xeon parts as added protection against alias-based attacks.
Why the WireTap results matter for enclaves and blockchains
Because DCAP attestation underpins trust establishment for SGX-backed services, key extraction can let an attacker masquerade as a trusted platform, forge quotes, and potentially decrypt “confidential” workloads in some decentralized systems that assume SGX attestation as ground truth. This realigns the risk model for blockchain or Web3 projects that rely on SGX for confidential smart contracts and storage proofs.
Historically, enclave threats centered on software: Foreshadow, cache-timing, and page-fault attacks. WireTap, however, leverages the off-chip memory bus, echoing prior research that showed the feasibility of off-chip observation against enclaves.
Mitigation and practical outlook for SGX/WireTap
From a defender’s standpoint, the first question is threat model. WireTap assumes hands-on physical access to the server and the ability to insert an interposer. In colocation, hostile supply chains, or insider-risk scenarios, that assumption is realistic. Therefore, platform owners should:
-
Treat SGX as not protecting against physical interposers; harden physical security, tamper evidence, and custody.
-
Prefer platforms with memory-integrity protections (e.g., Intel TME-MK) where relevant; validate attestation policies accordingly.
-
Implement key rotation and attestation revocation playbooks; don’t assume attestation keys are immutable.
-
Reassess reliance on attestation for financialized protocols (blockchain, storage proofs), and design secondary trust anchors.
FAQs
What’s the essence of the WireTap attack?
A passive DDR4 bus interposer captures encrypted traffic during enclave signing. By correlating ciphertext patterns, the attacker derives the ECDSA nonce and then the private attestation key.
Does WireTap break all SGX protections?
No. It violates assumptions about physical access, not SGX’s logical isolation. Intel states such interposer attacks are out of scope for SGX’s protection boundary.
Is there a CVE?
Intel says no CVE is planned because the threat model excludes physical interposers; instead, consider platform choices and integrity-protected memory features.
What should blockchain projects using SGX do?
Assume attestation keys can be stolen with physical access. Implement secondary verification, key rotation, and on-chain controls that don’t rely solely on SGX quotes.