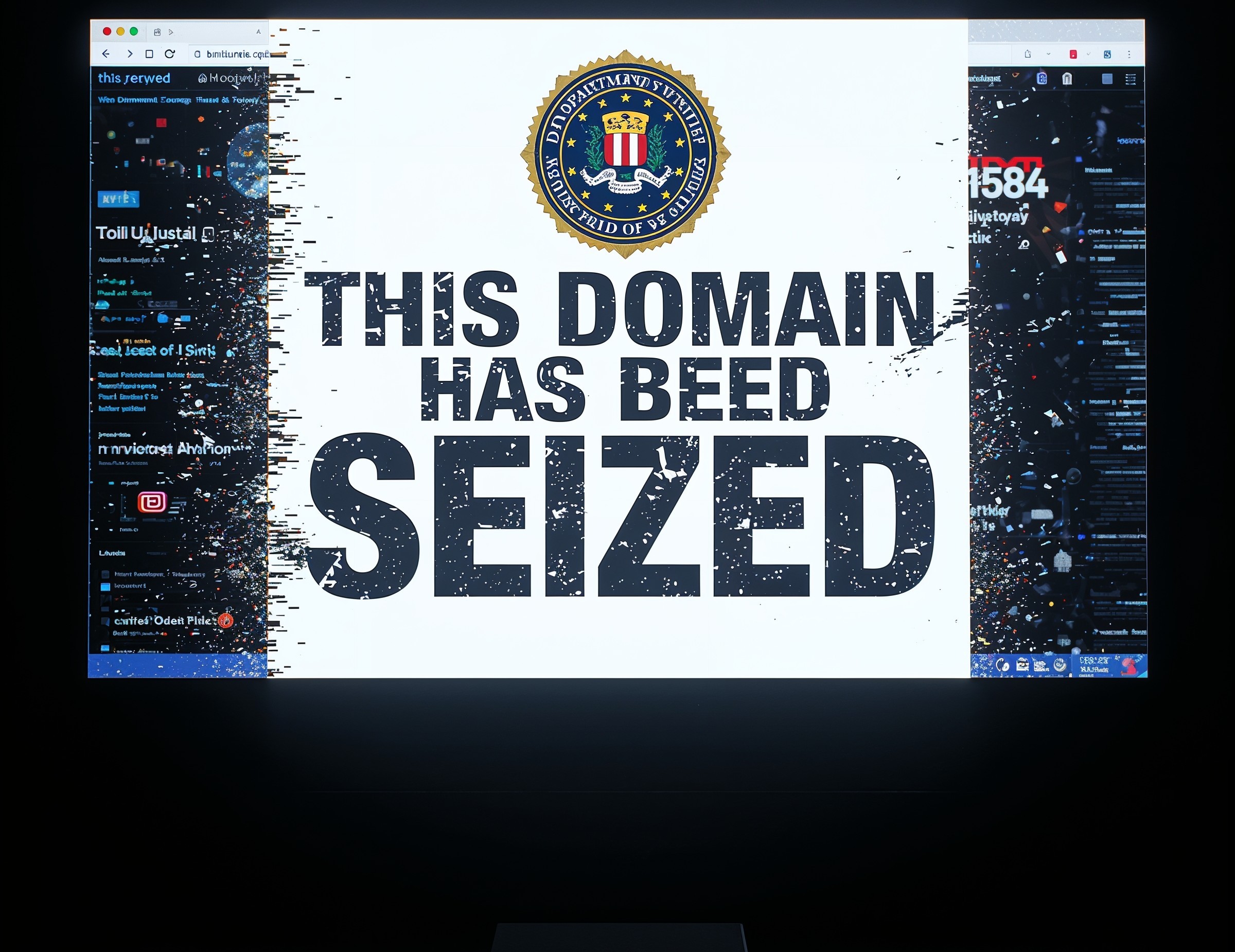
Federal law enforcement agencies have taken down a massive data-extortion platform operated by ShinyHunters, one of the most persistent cybercriminal groups in recent years. The site, which impersonated Salesforce, hosted stolen corporate data and served as a ransom negotiation portal.
The takedown represents a landmark action in the fight against global cyber extortion campaigns targeting major cloud service providers.
How the Salesforce Extortion Scheme Operated
The attackers built a Salesforce-branded ransom interface that convinced victims they were communicating through legitimate CRM channels. Stolen data was displayed as “proof of breach,” followed by automated ransom demands between $100,000 and $1.5 million in cryptocurrency.
Moreover, ShinyHunters weaponized automation sending simultaneous threats to corporate executives, then posting countdown timers on their extortion dashboards to pressure payment.
The portal was linked to multiple dark web marketplaces where additional stolen data was auctioned to buyers using Monero and Zcash.
FBI and Europol Coordinate the Global Seizure
The FBI, Europol’s EC3, and the UK National Crime Agency executed synchronized raids on data centers across three countries, seizing backend servers used to manage ransom payments and host leaked databases.
In addition, the FBI confirmed seizing several Tor and clear-net domains, each now displaying seizure notices citing violations of U.S. and international cybercrime statutes.
Officials described the takedown as “a high-value disruption” to a group responsible for data theft campaigns across North America, Europe, and Asia.
The ShinyHunters group emerged in 2020, known initially for selling stolen user databases from Tokopedia, Wattpad, and AT&T. Over time, it evolved into a data-leak marketplace where affiliates could upload and monetize stolen records.
By 2024, the group had pivoted toward direct corporate extortion, mimicking legitimate brands like Salesforce, Okta, and Microsoft 365 to maximize psychological leverage.
No Breach of Core Systems
Salesforce confirmed that no breach of its internal infrastructure occurred. The extortion site merely used Salesforce’s branding and simulated dashboards to deceive victims into believing the data originated from its systems.
A company spokesperson stated:
“The takedown does not involve any compromise of Salesforce systems. Attackers reused previously stolen data from unrelated breaches.”
Tactics Used by ShinyHunters
Analysis by digital forensics experts revealed the group’s tactics included:
-
Credential stuffing attacks on corporate SaaS platforms.
-
Phishing pages modeled after Salesforce login forms.
-
Data aggregation scripts to merge previously breached datasets.
-
Crypto wallet rotation for laundering ransom payments.
Furthermore, the attackers deployed automation bots to re-upload seized content to mirror sites within hours, showcasing remarkable operational resilience.
Using blockchain tracing and DNS overlap analysis, investigators linked the extortion portal’s domains to servers previously involved in credential-theft campaigns.
Additionally, unique SSL certificate reuse patterns and Tor-to-proxy relay identifiers revealed links to infrastructure hosting the “DataStorm” and “LuxLeaks 2024” marketplaces.
This digital fingerprinting allowed simultaneous cross-border seizures, minimizing server migration or data deletion risk.
Impact of the Operation
The seizure destabilized several affiliate ransomware and extortion networks that relied on ShinyHunters’ marketplace.
Consequently, industry watchers anticipate a temporary drop in enterprise data-leak extortion attempts. However, copycat groups often re-emerge under new branding a common pattern across the cybercrime ecosystem.
How Enterprises Can Protect Against Extortion Campaigns
To mitigate exposure, experts recommend:
-
Implement brand monitoring for spoofed domains.
-
Enforce MFA on all SaaS logins.
-
Audit credential hygiene quarterly.
-
Deploy zero-trust controls on cloud systems.
-
Report extortion attempts directly to authorities.
Ultimately, strong identity management, incident readiness, and information-sharing partnerships can significantly limit an organization’s risk surface.
The dismantling of the ShinyHunters’ extortion infrastructure represents a major step in law enforcement’s battle against cross-border cybercrime. It underscores the power of coordinated intelligence, blockchain analytics, and global cooperation.
In essence, this operation demonstrates that even agile, decentralized threat actors remain vulnerable to persistent digital forensics and multinational response.
FAQs
Q1. Who are the ShinyHunters?
A cybercrime collective behind large-scale corporate data theft and extortion campaigns active since 2020.
Q2. Was Salesforce hacked?
No. Attackers used Salesforce branding and reprocessed data from prior breaches.
Q3. How did the FBI trace the infrastructure?
Through DNS correlation, blockchain wallet tracing, and server metadata analysis.
Q4. What should companies do if extorted?
Avoid paying, document communications, and report immediately to law enforcement.
Q5. Will this stop similar campaigns?
Not permanently. The takedown may cause temporary disruption, but successors typically reappear under new aliases.