Pass-the-Hash thrives when the same local administrator password appears on many machines and when admins sign in everywhere with the same high-privilege identity. In small Active Directory domains, you can shut that down quickly. Rotate each device’s local admin secret with Windows LAPS, then enforce a simple tiered administration model so credentials never roam across risk levels. Do both in concert, and lateral movement loses its easiest path.
Pass-the-Hash Exploits in Small ADs
Small teams often inherit flat administration and shared local admin passwords because “it’s faster.” Attackers love that. After a single workstation compromise, they dump credentials, replay a reused hash against a nearby device, pivot to a server, and push toward Domain Admin. Because the hash equals a password for NTLM authentication, tools never need to reveal the clear-text secret.
As a result, one foothold can become many, and it can do so silently if you reuse credentials or allow privileged accounts to sign in broadly. Therefore, your goal is simple: make each machine’s local admin password unique and short-lived, and keep high-privilege accounts confined to where they belong.
Windows LAPS: Unique, Rotated Local Administrator Passwords
Windows LAPS (the modern, built-in solution) manages a per-device local administrator password, rotates it on a schedule, and stores the secret in your directory with strict read controls. Because every machine now carries a different local admin password, a stolen hash from one host cannot unlock the next. Unlike the older, legacy LAPS, Windows LAPS integrates natively and supports both Active Directory and Entra ID policy paths. It adds helpful behavior such as rotating after a successful directory read, expiring secrets on demand, and managing DSRM passwords on domain controllers. You don’t need the legacy client to use it; in fact, on supported OS versions, you should migrate away from legacy LAPS entirely.
However, LAPS is not a silver bullet. It won’t stop attackers from replaying tokens you expose during privileged sign-ins, and it won’t fix administrators who log on to the wrong tier. Consequently, you pair LAPS with a tiered admin model and with credential protections like Credential Guard and LSA Protection.
Active Directory Tiering for Small Teams: Tier 0 / Tier 1 / Tier 2
Small organizations rarely have time for sprawling identity projects. Fortunately, a lean tier model delivers most of the benefit with modest effort.
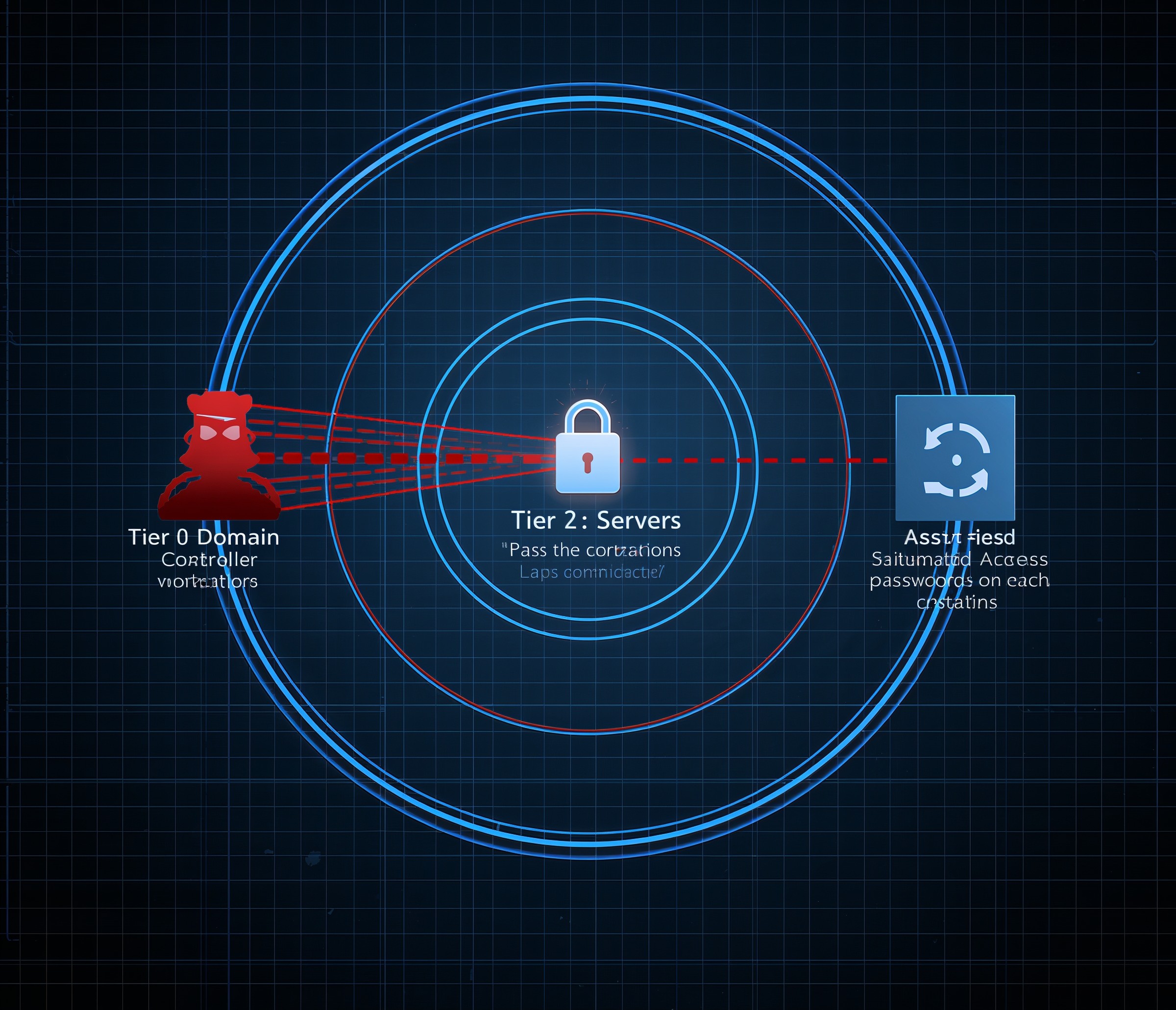
First Tier 0 hosts and identities: domain controllers, ADFS/Entra Connect, PKI, and identity infrastructure. Tier 0 administrators use only Tier 0 accounts and sign in only to Tier 0 systems.
Second Tier 1 hosts and identities: application servers, file/print, SQL, and critical business services. Tier 1 admins sign in only to Third Tier 1, never to user workstations, and never with Tier 0 credentials.
Fourth Tier 2 hosts and identities: user workstations and VDI. Helpdesk and desktop support operate here. No Tier 1 or Tier 0 accounts sign in at Tier 2, ever.
This separation seems strict; nevertheless, it reduces risk immediately. Attackers rely on credential reuse and over-privileged logons to move upward. When your rules stop high-privilege credentials from touching lower-trust systems, common attack chains fail by design.
How LAPS and Tiering Work Together to Stop Pass-the-Hash
When Tier 2 workstations each hold unique local admin secrets managed by LAPS, a stolen hash from one endpoint doesn’t unlock its neighbor. Because Tier 1 servers do the same, an attacker cannot replay a Tier 2 hash to spread through servers. Meanwhile, Tier 0 systems remain off-limits to Tier 2 and Tier 1 credentials entirely. Even if a local admin hash leaks, the model prevents upward reuse, and LAPS resets the secret on schedule. Therefore, the combined effect is powerful: less credential reuse, fewer viable lateral steps, and less time for attackers to escalate.
Deploying Windows LAPS in an AD Domain (Small-Shop Path)
Start with prerequisites: ensure supported Windows versions, confirm schema readiness for Windows LAPS attributes, and decide where to back up secrets (Active Directory or Entra ID). Then, configure policy centrally. Using Group Policy, set the rotation period, password complexity, the managed local admin account name, and who can read the secret.
For small teams, adopt just-in-time access to LAPS reads helpdesk staff request a read when they need to unlock a device, and the system rotates the password after use. Because secrets change automatically, you avoid sticky notes, shared vault entries, and all the legacy baggage that feeds Pass-the-Hash.
If you run legacy LAPS, plan a measured migration. Test Windows LAPS in a small OU, verify rotation and retrieval behaviors, and retire the old client once your devices move over. Keep an eye on precedence between legacy and modern settings during the transition so policies do not collide.
Create and Enforce the Tiers Without Heavy Overhead
Draw three OUs that reflect Tier 0, Tier 1, and Tier 2. Place the corresponding devices in each OU and scope administrative groups and policies to match. Next, create separate admin personas one per tier for each administrator. Limit where these accounts can log on. In practice, this means your Tier 0 admin account cannot sign in to servers or workstations, and your Tier 1 admin account cannot touch workstations.
You still sign in as your standard user account for email or browsing; you elevate only within the correct tier when needed. Because small teams juggle many roles, document a short decision tree: which account to use, which systems it can touch, and how to request temporary access if an exception arises.
Reduce the Credential Theft Surface with Platform Controls
Because Pass-the-Hash begins with credential theft, strengthen the system boundary around secrets. Turn on Windows Defender Credential Guard, which isolates hashes and Kerberos tickets with virtualization-based security. Additionally, enable LSA Protection (also called RunAsPPL) to prevent code injection into the Local Security Authority process that manages sensitive operations.
If you use Remote Desktop, prefer Remote Credential Guard so your credentials stay on the client and never land on the remote host. These platform protections do not replace LAPS or tiering; however, they shrink the window in which attackers can harvest material for replay.
Operations That Keep Pain Narrow for Small IT
Because you rotate local admin passwords, you need a clean retrieval path. Use a short, auditable workflow: a ticket or task triggers a just-in-time read; the technician retrieves the secret from directory; automation rotates the password after use. For break-glass scenarios, store an emergency access account and process offline, test it quarterly, and rotate its secret immediately after use.
Because two-person teams cannot babysit policies all day, schedule checks rather than chasing alerts. Weekly verification of rotation health, monthly checks for mis-scoped logon rights, and quarterly reviews of exceptions keep the model intact without consuming the whole week. If a legacy line-of-business server cannot run Credential Guard or blocks LSA Protection, compensate: shorten the LAPS rotation, restrict admin logon locations further, and treat that host as higher risk in monitoring.
Verification: Prove the Pass-the-Hash Paths Are Closing
Trust but verify. First, confirm that each machine truly holds a unique local administrator secret. Check a sample of devices with the LAPS UI or PowerShell and confirm different timestamps and password values. Second, validate your logon restrictions. Attempt to sign in to a workstation using a Tier 1 admin account; the system should refuse. Attempt to RDP from a workstation to a server with a Tier 2 account; it should fail. Third, watch for the right events.
Successful and failed admin logons (4624/4625) on Tier 2, logon types 3 and 10 in odd places, and repeated use of the built-in local administrator account all deserve attention. Because attackers experiment, rapid, repeated authentication attempts that hop between machines should trigger questions, even when they succeed.
Handling Legacy and Exceptions Without Collapsing the Model
You will meet exceptions. Some imaging tools expect the same local admin password everywhere. Some vendor appliances do not support modern protections. Do not abandon the model for them. Instead, document the exception, restrict where it sits, reduce who can reach it, and shorten the LAPS rotation window aggressively. If Credential Guard or LSA Protection cannot run, compensate by isolating the system network-wise and by using stronger just-in-time administrative sessions. Because exceptions often linger, review them on a fixed cadence and push upgrades when vendors finally support the right controls.
Business Outcomes: Fewer Incidents, Cleaner Audits, Calmer Days
LAPS plus tiering rarely makes headlines. Yet it blocks the most common escalation path in Windows estates. You shrink the blast radius of any single compromise. You also cut the number of accounts and systems touched during an incident, which speeds containment and lowers cleanup costs. As you rotate secrets and restrict where admins sign in, the audit trail becomes clearer. Uptime improves as well. Even search visibility benefits over time: fewer malicious redirects, fewer domain-wide outages, and fewer trust signals that damage your brand.
Practical, Lightweight Rollout Plan for Small ADs
Day 1: Enable Windows LAPS for a pilot OU of workstations. Set a rotation interval that fits helpdesk workflows. Define read rights narrowly.
Day 2: Create Tier 0, Tier 1, and Tier 2 OUs. Move a small device set into each OU. Bind logon restrictions to match the tiers.
Day 3: Create separate admin personas. Limit where each persona can log on. Test sign-in behavior and confirm the boundaries hold.
Week 1: Enable Credential Guard and LSA Protection where supported. Then test Remote Credential Guard for RDP.
Week 2: Extend LAPS to servers and domain controllers. Enable DSRM password management.
Week 3: Document exceptions, tune monitoring, and publish a short runbook what account to use, which tier it belongs to, and how to handle break-glass access.
Small domains can shut down Pass-the-Hash fast without enterprise budgets. Deploy Windows LAPS so every device holds a unique, rotated secret. Enforce a three-tier admin model so privileged identities never drift into low-trust territory. Turn on Credential Guard, LSA Protection, and Remote Credential Guard to reduce credential exposure. Then verify progress by testing sign-in boundaries and watching for suspicious lateral moves. These steps use platform features you already own, so you gain strong control with minimal overhead.
FAQs
Is LAPS alone enough to stop Pass-the-Hash?
No. LAPS kills lateral reuse of local admin hashes; however, it doesn’t stop token replay from privileged sessions. Pair it with tiering, Credential Guard, LSA Protection, and strict logon boundaries so high-privilege credentials never land on low-trust systems.
Do I still need Credential Guard if I rotate local admin passwords?
Yes. Credential Guard isolates secrets and reduces the chance that an attacker can extract material for replay during a privileged session. Because it works at the platform layer, it reinforces LAPS and tiering.
How often should I rotate the local administrator password?
Choose a rotation period that balances security and operations. Many small teams start with 7–14 days and shorten intervals for sensitive systems or for any host under an exception. Rotate immediately after a read to cut exposure further.
Can two administrators really run a tiered model?
Yes. Use separate personas and a short, documented process for just-in-time elevation. Because your boundaries are simple—Tier 0, Tier 1, Tier 2—you avoid complex tooling while still blocking upward movement.
What breaks when I enforce strict logon restrictions?
Old habits, mostly. Some tools expect admins to sign in everywhere, and some scripts assume reused local admin passwords. Address the scripts, not the model. Because the model reduces risk dramatically, treat exceptions as temporary and compensate while you fix root causes.
How should I handle vendors and remote support?
Give vendors a path that respects tiers. Require unique local admin passwords via LAPS, time-boxed access, and a monitored connection. If they must use RDP, prefer Remote Credential Guard so vendor credentials never land on your servers.