Threat actor Detour Dog has upgraded its tactics. The group now operates a DNS-based malware distribution pipeline, pushing Strela Stealer through a network of compromised sites and TXT-encoded payload instructions. This new campaign marks a sharp evolution from simple redirects to a sophisticated, DNS-mediated command structure.
Background & Actor Profile
-
Detour Dog first appeared in mid-2023, known for injecting malicious JavaScript into WordPress sites. The scripts exfiltrated data and redirected users through Traffic Distribution Systems (TDS) that monetized fraudulent traffic.
-
According to Infoblox researchers, Detour Dog has since repurposed its infrastructure to control a distributed malware network through DNS TXT records acting as covert communication channels.
-
The actor’s shift from affiliate scams to malware delivery demonstrates a growing interest in persistent, scalable infection ecosystems.
Attack Architecture & Flow
The Detour Dog attack chain is built around DNS as its backbone.
-
The victim unknowingly interacts with a compromised site hosting a malicious SVG file.
-
The SVG initiates a DNS TXT request to a Detour Dog-controlled name server.
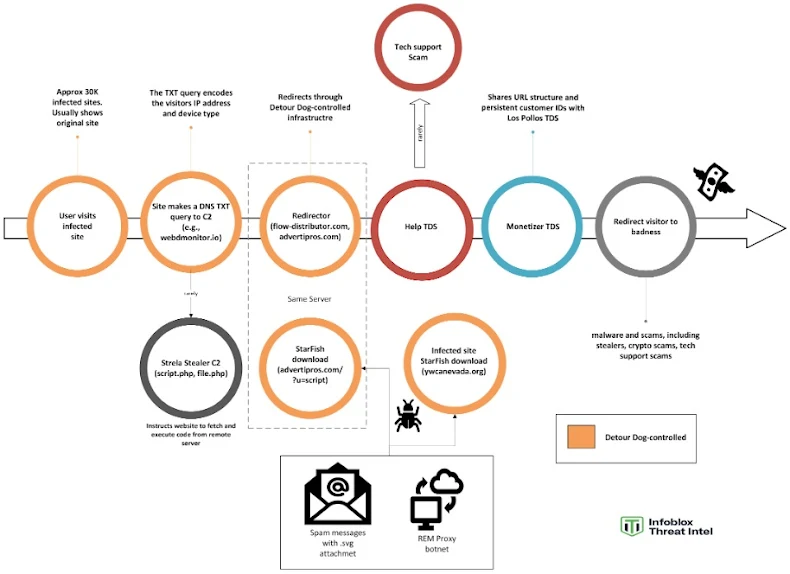
-
The response contains Base64-encoded TXT data, sometimes prefixed with “down” — a signal to fetch payloads.
-
Once decoded, the victim system retrieves the StarFish downloader from the actor’s controlled staging server.

-
StarFish then downloads and deploys Strela Stealer, a known information-stealing malware targeting browser-stored credentials and crypto wallets.
Infoblox reports that over 69% of StarFish domains belong to Detour Dog, establishing clear ownership of the malware delivery pipeline. Botnets such as REM Proxy and Tofsee appear to assist in distributing the initial malicious documents, further complicating attribution.
Stealth and Persistence
Detour Dog’s infrastructure is deceptively quiet:
-
Roughly 90% of DNS queries produce benign responses; 9% trigger advertising redirects, while 1% execute code.
-
Compromised websites continue to serve normal content, avoiding suspicion.
-
The DNS C2 network is modular each domain handles specific phases (command, payload, relay), masking true origins.
-
During July–August 2025, Infoblox and Shadowserver sinkholed key Detour Dog domains, but replacement infrastructure emerged within weeks.
Technical Insights & Design Complexity
The campaign’s ingenuity lies in its multi-layered use of DNS:
-
Command Channel: DNS TXT records transmit encoded tasking data.
-
Payload Relay: Compromised sites act as middlemen, concealing real hosting nodes.
-
Trigger Mechanism: The “down” token instructs download initiation, streamlining distribution.
-
Obfuscation: Base64 and response randomization complicate detection by signature-based tools.
This modular, DNS-powered structure enables geo-filtering, timed activation, and stealth, making it highly resistant to static analysis.
Detection Engineering & Defense Strategy
As defenders, countering Detour Dog’s DNS abuse requires both network-centric monitoring and behavioral analytics:
-
Log DNS TXT activity from web servers especially high-entropy responses or unusual subdomain patterns.
-
Correlate DNS telemetry with endpoint logs to identify command sequences and payload downloads.
-
Enforce strict egress filtering limit web servers from resolving arbitrary external domains.
-
Leverage passive DNS and threat intel feeds to enrich indicators with context.
-
Monitor for StarFish-related artifacts, including command strings, mutexes, or domains embedded in binary metadata.
-
Integrate YARA detection targeting DNS TXT parsing routines or encoded “down” prefixes.
Defensive maturity lies in recognizing that malware can ride legitimate protocols DNS, HTTPS, or NTP without triggering signature alarms.
Multiple threat intelligence vendors suspect Detour Dog has ties to an Eastern European criminal cluster that previously operated under the FakeUpdate (SocGholish) umbrella.
Correlations include shared domain naming conventions, similar payload encryption routines, and identical TDS configuration files.
While attribution remains unconfirmed, this linkage reinforces that traditional malvertising operators are evolving into infrastructure providers for stealer and loader families.
volving DNS Abuse
Given the growing attention from defenders, expect threat actors to:
-
Move from TXT-based DNS commands to DoH (DNS-over-HTTPS) for greater concealment.
-
Experiment with cloud DNS services and public resolvers to blend malicious queries into legitimate noise.
-
Automate payload staging through decentralized content platforms or IPFS-like storage.
As detection frameworks adapt, adversaries will continue leveraging ubiquitous internet protocols to build covert control layers.
Detour Dog’s campaign is a case study in protocol abuse turning the internet’s most fundamental service into a malware delivery mechanism.
It illustrates how attackers continuously innovate beneath the visibility threshold of conventional detection, compelling defenders to move toward behavioral, correlated, and context-driven analysis.











2 thoughts on “How Detour Dog Exploits DNS TXT for Advanced Malware Delivery”