A new cyber threat known as CometJacking is rapidly spreading across the internet, turning unsuspecting users’ devices into proxy nodes with just a single click. The campaign abuses WebSocket technology in browsers to hijack bandwidth and proxy connections all without installing malware or requiring user permissions.
This stealthy operation demonstrates how modern browsers, when misused, can function as powerful distributed networks for threat actors. Once the victim opens a malicious webpage, their device silently begins routing traffic for cybercriminals.
Anatomy of the Attack
Security researchers from Guardio Labs discovered the ongoing CometJacking campaign in early October 2025. The operation relies on a legitimate proxy service called Bright Data (formerly Luminati), which offers bandwidth-sharing capabilities. Attackers exploit this infrastructure by injecting rogue JavaScript code into compromised websites or through deceptive links on social media and email.
When a user lands on a malicious page, the embedded script establishes a WebSocket connection to Bright Data’s network. This connection enables continuous two-way communication between the browser and the proxy system. From that moment, the victim’s computer begins forwarding data packets effectively transforming it into a relay node for cybercriminal activities.
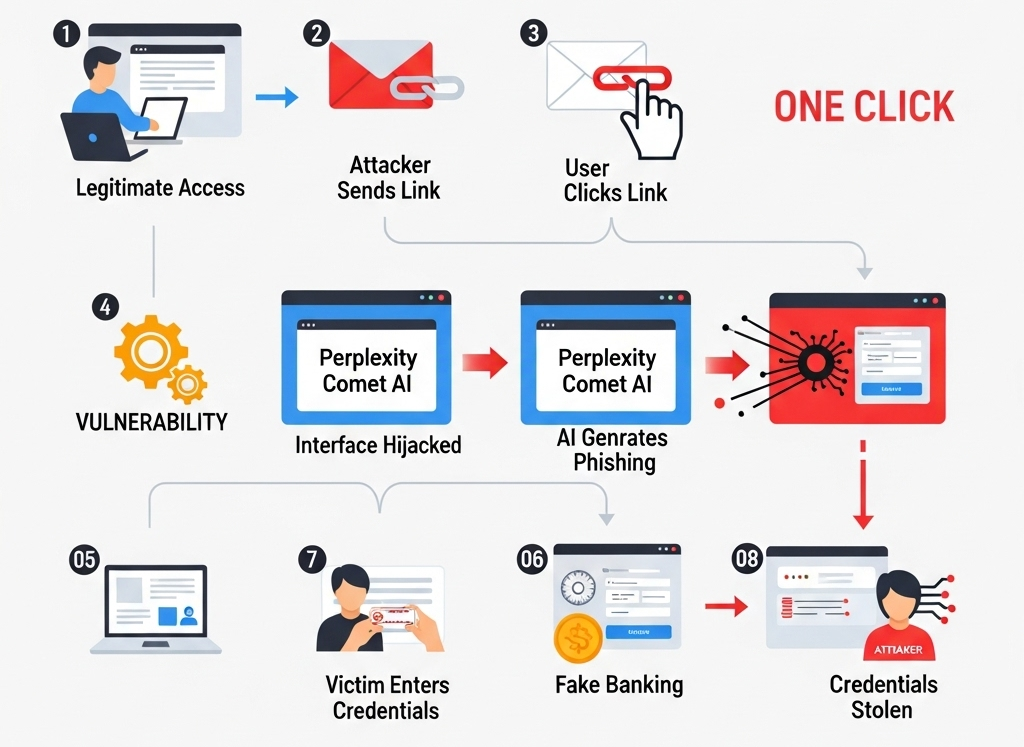
The attack requires no downloads or system-level access. It leverages standard browser APIs, making it extremely difficult to detect. As long as the browser tab remains open, the attacker can use the victim’s bandwidth and IP address for malicious purposes such as masking identities, launching scraping operations, or facilitating online fraud.
The exploit uses a single line of JavaScript to initiate the WebSocket handshake. Afterward, the attacker’s command server injects parameters to authenticate the connection with the proxy network. Because the traffic appears legitimate, network monitoring tools rarely flag it as suspicious.
Researchers also observed that CometJacking pages disguise themselves as harmless blogs, download sites, or news portals. Some of these pages even embed iFrames or advertisements to distract the victim from noticing high CPU or bandwidth usage. In most cases, the impact ends once the tab is closed. However, advanced versions can re-establish connections automatically through service workers, keeping the proxy alive longer.
Stealth, Monetization, and Risks
Unlike traditional botnets, CometJacking doesn’t rely on binary infections or command-and-control malware. Instead, it monetizes browser-level control. Attackers sell hijacked connections to underground proxy brokers or use them to route traffic anonymously through unsuspecting victims.
The consequences are significant. Victims risk having their IP addresses tied to fraudulent or illegal activities. Corporate users may also face compliance violations if company endpoints are unknowingly rerouted through malicious proxy networks. Moreover, the campaign’s reliance on standard web protocols makes it almost invisible to most endpoint detection solutions.
Therefore, this attack model reflects a new phase of malware-less exploitation, where traditional defenses antivirus, endpoint firewalls, and signature-based detection offer limited protection.
Defensive Measures and Mitigation
Organizations should strengthen their defenses at the browser and network layers. Browser isolation technologies, real-time script analysis, and strict content filtering can reduce exposure to malicious JavaScript. Security teams must also enforce DNS filtering and WebSocket monitoring to detect abnormal connections.
From a policy perspective, companies should disable peer-to-peer proxy features in browsers and educate users about suspicious sites that request continuous background connections. Moreover, integrating behavioral analysis into Secure Web Gateways (SWG) can help flag prolonged browser sessions generating proxy-like traffic patterns.
For individual users, awareness is crucial. Avoiding untrusted websites, blocking third-party scripts, and keeping browsers updated are simple yet effective ways to prevent browser-based hijacking.
CometJacking showcases how browser capabilities can be weaponized at scale. As browsers evolve toward greater interactivity and persistent connectivity, threat actors will continue exploiting these features for profit.
In the long run, attackers may combine CometJacking with malvertising networks or phishing campaigns, embedding scripts into legitimate ad platforms or compromised CDN resources. Consequently, defending against this trend requires collaboration between browser vendors, web developers, and cybersecurity researchers.
The campaign signals a paradigm shift attackers are moving away from malware executables and focusing on living-off-the-browser techniques.
FAQs
Q: What is CometJacking?
A: CometJacking is a browser-based exploitation technique that hijacks a user’s internet connection via WebSockets, turning the browser into a proxy relay.
Q: How does the attack work?
A: When users visit a compromised website, injected JavaScript connects their browser to a proxy network, allowing attackers to route traffic through it.
Q: Is malware installed on the device?
A: No. The attack runs entirely within the browser and doesn’t require software downloads or administrative privileges.
Q: How can users protect themselves?
A: Avoid suspicious sites, disable background connections, use script blockers, and keep browsers up to date to prevent unauthorized WebSocket use.
Q: What can organizations do to mitigate the threat?
A: Enforce WebSocket monitoring, implement browser isolation, and use DNS filtering to detect proxy-like traffic originating from browsers.











One thought on “CometJacking Turns Browser Sessions into Covert Proxy Channels”