New Ollama and NVIDIA Flaws Expose AI Stacks Fix Fast
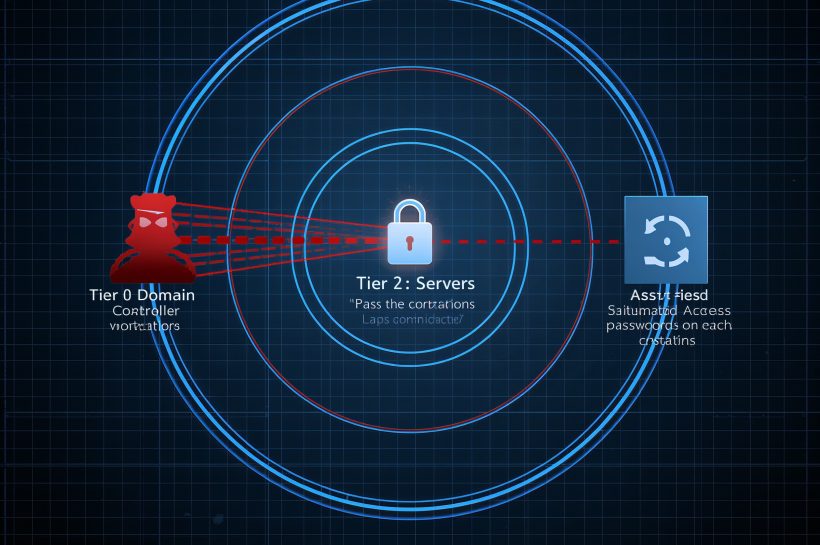
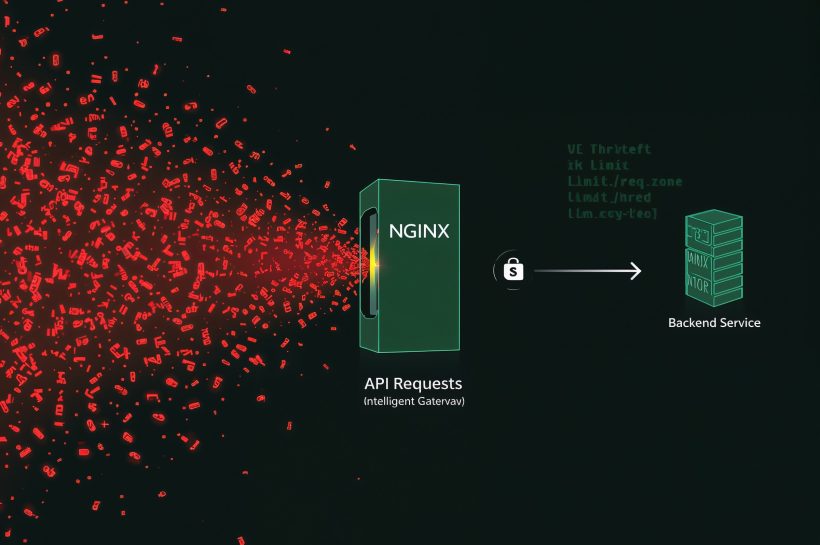
Exposed Ollama APIs and a critical NVIDIA Container Toolkit flaw raise the stakes for AI infrastructure. Authenticate Ollama, close public 11434, and patch NCT to stop container escapes. Stream LLM and runtime logs off-box, rotate tokens, and validate least-privilege settings to keep model IP and GPU workers safe.