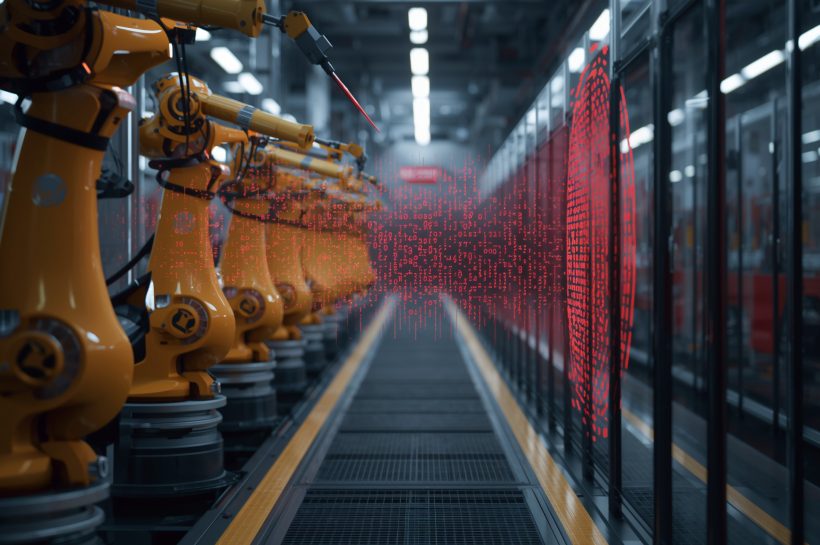
2025 Manufacturing Under Siege: Cyber Threats Reach Levels
Manufacturers face the most dangerous cyber landscape in their industry’s history. Attackers now target OT systems, supply chains and intellectual property with unprecedented sophistication, creating widespread operational and financial impact.