CERT-UA Issues Alert on CabinetRAT Backdoor Cyber Threat
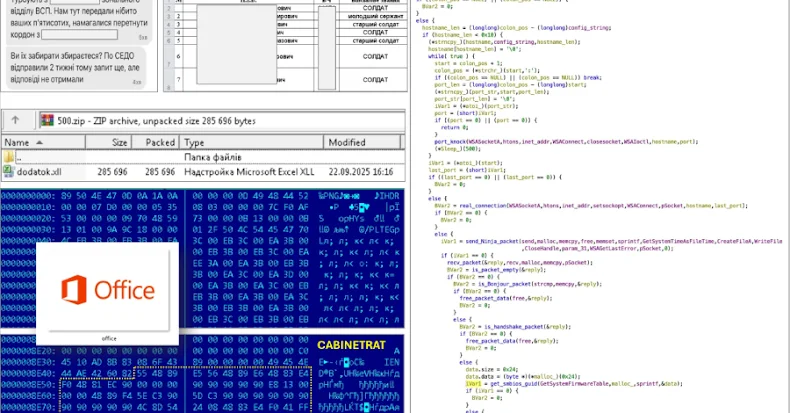
Ukraine’s CERT-UA has warned that CabinetRAT backdoor malware is being actively deployed in cyber espionage campaigns targeting government and critical networks.

Ukraine’s CERT-UA has warned that CabinetRAT backdoor malware is being actively deployed in cyber espionage campaigns targeting government and critical networks.

Microsoft’s December 2025 Patch Tuesday delivers critical security updates — 56 vulnerabilities across Windows, Office, Exchange and more including three zero-day flaws. Attackers exploited at least one, making immediate patching vital for enterprise and personal systems alike.

WhatsApp has introduced a new lockdown-style security mode designed to protect users from sophisticated digital threats by restricting high-risk features and hardening the platform against abuse.

Some Windows 10 ESU devices fail to install the KB5068781 update, rolling back with error 0x800f0922. Microsoft now lists this as a known issue that affects subscription-activated ESU systems managed through the Microsoft 365 Admin Center. Track affected devices, verify ESU activation, and plan for a servicing fix.

A MongoDB vulnerability tracked as CVE-2025-14847 highlights how weaknesses in access control handling can expose database environments to unauthorized access and data compromise.

Microsoft’s emergency out-of-band update (KB5070773) fixes a USB input failure in the Windows Recovery Environment that impacted Windows 11 and Server 2025 devices. This article explains the bug, affected platforms, and recommended actions for IT professionals.

Researchers documented CVSS 8.9 command injection in three official Claude Desktop extensions Chrome, iMessage, and Apple Notes. Because those connectors built AppleScript commands with unescaped user input, prompt injection could pivot from web content to local shell execution on macOS. Anthropic patched the issues. This analysis explains the exploit chain, the fixes, and the validation steps security teams should run to keep MCP servers safe.

A public PoC exploit for CVE-2025-32463 in Sudo has been released, enabling local privilege escalation to root. Linux users are urged to update to Sudo 1.9.16p1.

A widespread campaign exploited the Chrome Web Store to distribute 131 rebranded extensions that hijack WhatsApp Web for automated bulk messaging. These add-ons pose a significant risk to organizations and users alike, demanding immediate review of extension governance and messaging platform protections.

BADCANDY continues to compromise exposed Cisco IOS XE devices via CVE-2023-20198. Close the web UI exposure, patch now, rotate credentials, and verify eradication.