
Confucius APT Unleashes WooperStealer, Anondoor in Pakistan
Confucius hackers launched a phishing campaign in Pakistan deploying WooperStealer and Anondoor malware using PPSX and LNK files to compromise sensitive systems.

Confucius hackers launched a phishing campaign in Pakistan deploying WooperStealer and Anondoor malware using PPSX and LNK files to compromise sensitive systems.

Hackers breached Red Hat and GitHub in coordinated attacks and stole customer data, underscoring risks even in widely trusted development platforms.
Google Mandiant has launched an investigation into a new cyberattack campaign targeting Oracle systems, raising alarms over advanced threat activity and enterprise risks.

The PyPI “SoopSocks” package claims to be a SOCKS5 proxy solution but conceals backdoor capabilities, enabling attackers to control compromised systems remotely.

A newly discovered Android banking trojan combines overlay attacks with a stealthy hidden VNC server to gain full remote control over compromised devices.
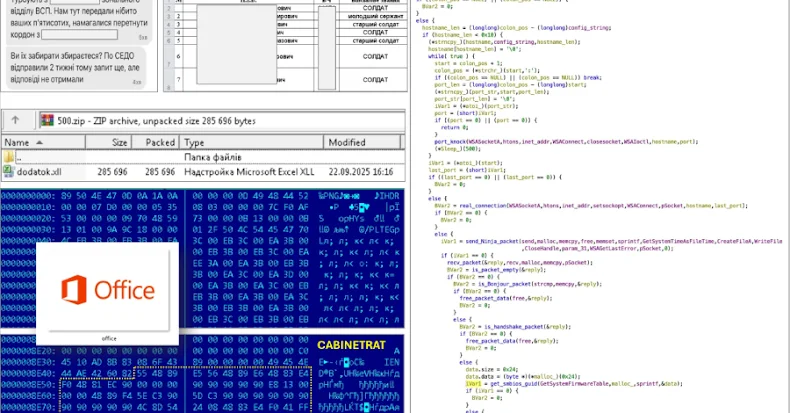
Ukraine’s CERT-UA has warned that CabinetRAT backdoor malware is being actively deployed in cyber espionage campaigns targeting government and critical networks.

APT35 hackers, linked to Iran, are conducting cyberattacks against global government and military organizations, using spear-phishing and malware for espionage.

Security researchers have identified a critical zero-day flaw (CVE-2025-41244) affecting VMware Tools and VMware Aria. The bug enables local privilege escalation to root, a dangerous step in potential exploitation chains. The issue lies in service discovery mechanisms built into VMware, which allow guest and management systems to interact. Attackers are abusing this trust to escalate…

EvilAI operators are hiding malware in legitimate-looking AI tools that appear functional and signed, enabling reconnaissance, browser data exfiltration, and encrypted C2 communication across global targets.

A sophisticated cyber campaign used DLL side‑loading to deliver a hybrid PlugX variant and the Bookworm backdoor to telecom and ASEAN networks, revealing renewed tactics by China‑linked threat actors.