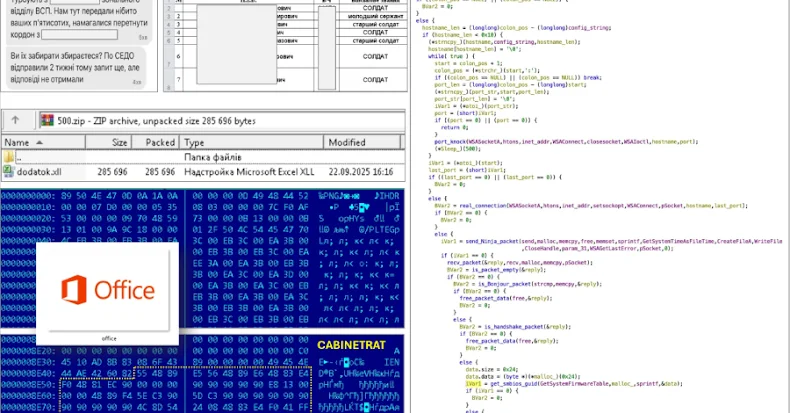
Algorithmic Fail: TikTok Sends Minors Explicit Search Suggestions
Despite enabling safety filters, child accounts on TikTok have received explicit content suggestions via search. This investigation reveals algorithmic failures and urges stronger oversight for youth protection.