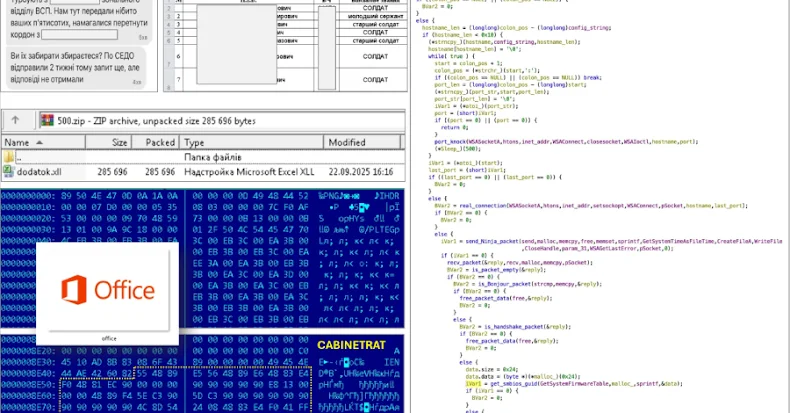
Net-CAPI: The Stealth Backdoor Hidden in Windows CryptoAPI
A newly discovered backdoor, dubbed Net-CAPI, has infiltrated multiple Russian government networks by hijacking Windows cryptographic services. Analysts believe the tool, developed by a sophisticated threat group, uses advanced evasion and persistence methods to hide within legitimate system operations—making detection nearly impossible.