
Apple Bug Bounty Adds Bonus for Lockdown Bypass Finds
Apple has expanded its bug bounty program to reward researchers up to $2 million for zero-click exploit chains. Bonuses for Lockdown Mode bypasses and beta findings may push payouts even higher.

Apple has expanded its bug bounty program to reward researchers up to $2 million for zero-click exploit chains. Bonuses for Lockdown Mode bypasses and beta findings may push payouts even higher.

A trivial surveillance password created an opening at one of the world’s most prominent institutions. Intruders gained awareness and timed their move because credential policy failed. This analysis delivers the signals, mitigations, and governance disciplines that stop repeats: rotation, MFA, segmentation, PAM for service accounts, and continuous validation for VMS and NVR stacks—without resorting to list spam or generic advice.
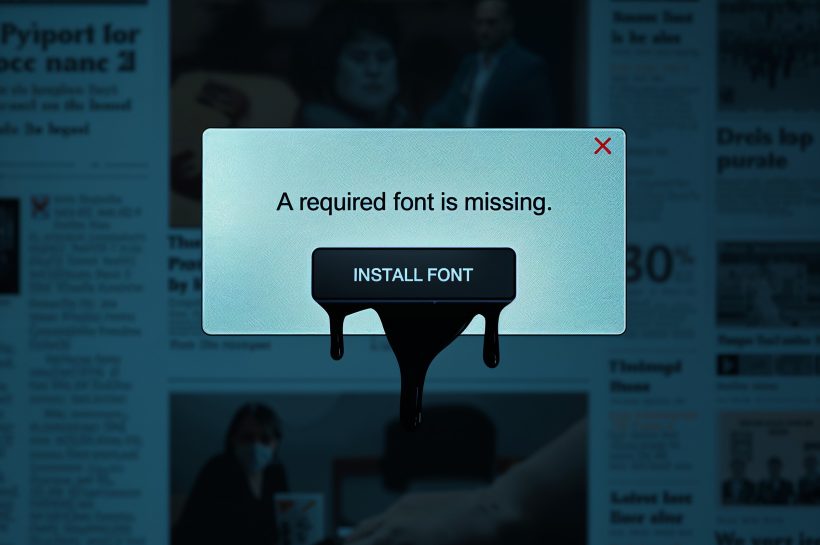
GootLoader reappeared with custom WOFF2 web-fonts that swap glyph shapes, so a gibberish string in source renders as a harmless-looking filename in the browser. Consequently, victims on SEO-poisoned WordPress sites download ZIP archives carrying JavaScript loaders that trigger rapid, hands-on compromises. Therefore, block risky downloads, hunt for loader execution, and harden WordPress and endpoints to cut dwell time and prevent domain-wide impact within hours.

macOS now attracts serious attention from nation-state and criminal actors, especially credential stealers. A new public dataset, Malet, and a static analysis tool, Katalina, give defenders large-scale visibility into Mach-O malware traits. Teams can use them to tune EDR, test vendor claims, and finally treat Mac fleets as first-class citizens.

A Russian-linked threat actor is hiding Stealc V2 infostealer inside Blender project files shared on 3D model marketplaces. By abusing Blender’s Auto Run Python Scripts feature, the campaign turns legitimate-looking character rigs into a delivery vector that steals browser, wallet, VPN and messaging credentials from creative workstations.
Attackers exploit CVE-2025-61932 in Lanscope Endpoint Manager clients to run code and move laterally. Patch MR/DA endpoints now and reduce internet exposure.