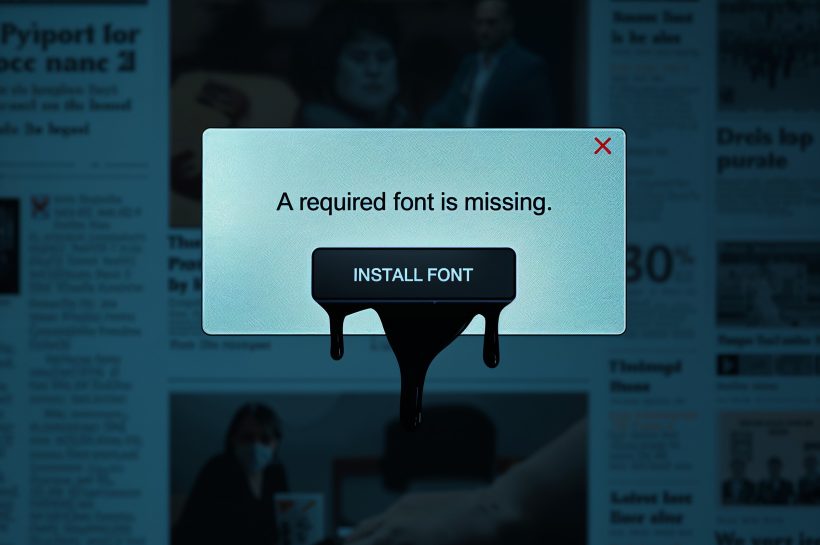
How the JackFix attack upgrades ClickFix social engineering
The JackFix attack marks the latest evolution of the ClickFix technique. By luring victims through fake adult sites into a full-screen Windows update screen, encoding Run-dialog commands, gating its payload URL, and dropping multiple infostealers through an obfuscated PowerShell script, JackFix sidesteps many earlier ClickFix mitigations and forces defenders to rethink how they handle browser-driven social engineering.