China‑linked threat actors launched a focused espionage campaign against telecommunications and ASEAN networks. They deployed a hybrid PlugX variant alongside the Bookworm RAT, using DLL side‑loading to bypass standard defenses.
This campaign stands out for combining legacy tools (PlugX) with newer modular components, increasing flexibility and evasion.
The Evolved PlugX Variant
Shared lineage with RainyDay / Turian families
The PlugX variant in this campaign preserves core traits: abuse of legitimate application loaders, XOR + RC4 + RtlDecompressBuffer decryption routines, and layered encryption.
Modular enhancements & configuration shifts
Unlike earlier PlugX versions, this variant can dynamically load plugins. One notable addition is a keylogger module. Its configuration format diverges from the RainyDay branch, making it harder to fingerprint against known signatures.
The Bookworm RAT: Modular and Stealthy
Bookworm acts as a fully modular backdoor framework. It supports:
-
Plugin-based extensions
-
Stealth communication with C2
-
File transfers and persistence
-
Blending into the environment using legitimate-looking domains
Its flexibility makes Bookworm a favored tool in multi-stage campaigns targeting strategic infrastructure.
The initial infection chain begins with a legitimate application (e.g. Mobile Popup Application). The threat actor replaces or appends a malicious DLL, enabling the loader to inject memory-resident payloads.
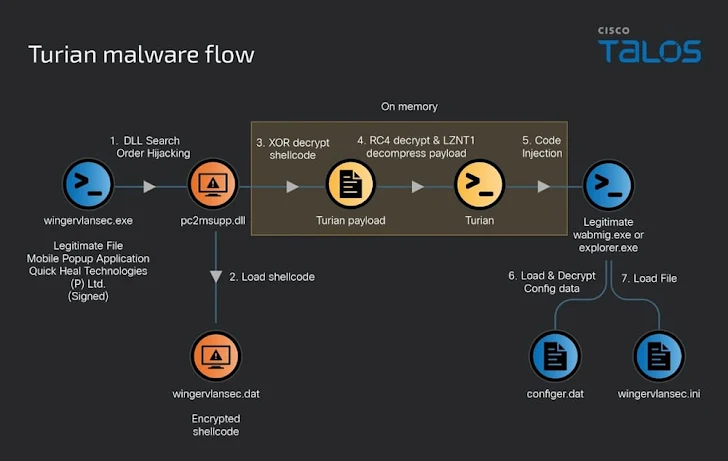
Once the DLL loads, decryption routines decrypt embedded payloads (PlugX / Bookworm) and execute them within memory, minimizing footprint on disk.
Analysts link this campaign to Lotus Panda (Naikon) and sibling groups like BackdoorDiplomacy and Cycldek. Evidence includes:
-
Target profile overlaps
-
Use of similar encryption routines
-
Code reuse and infrastructure alignment
Attribution confidence is moderate to high due to these multiple indicators and historical patterns.
| Type | Details |
| Domains | (list of known C2 / infrastructure domains) |
| File & DLL names | (legitimate app name + side‑loaded DLL) |
| Encryption routines | XOR, RC4, memory decompression |
| Behavior patterns | Unusual DLL loads, memory injection, decrypted payloads |
Mitigation & Defensive Tactics
-
Detect and block anomalous DLL load behaviors under legitimate executables
-
Deploy memory scanning via EDR to catch loaded payloads
-
Segregate and monitor network zones to contain lateral spread
-
Use domain filtering to block known C2 infrastructure
-
Threat hunt around reused encryption routines and plugin behavior
Strategic Insights & Lessons Learned
-
Attackers blend old tools (PlugX) with modular RATs (Bookworm) to increase adaptability
-
DLL side‑loading remains a powerful evasion vector
-
Encrypted payloads and dynamic plugin systems complicate signature-based detection
-
Layered defenses and threat hunting matter even more
This campaign shows that cyber espionage keeps evolving: threat actors are retooling classic malware with modular designs and leveraging DLL side‑loading to evade detection. Telecom and infrastructure defenders must assume any signed executable can be suspect, scrutinize DLL behavior, and maintain robust memory-based defenses.
FAQs
Q: What is PlugX malware?
A: PlugX is a backdoor that uses side‑loading techniques and modular plugins to execute commands, move laterally, and maintain persistence.
Q: What is the Bookworm RAT?
A: Bookworm is a modular remote access tool used by threat actors to load plugins, communicate with C2, transfer files, and evade detection.
Q: How does DLL side‑loading work?
A: Attackers exploit legitimate applications’ DLL loading behavior to trick them into loading malicious DLLs, which execute payloads from memory.
Q: How can organizations defend against such campaigns?
A: Use memory scanning, monitor for anomalous DLL loads, block known malicious domains, enforce network segmentation, and treat signed binaries with skepticism.










